Breaking News
Cloning Of Sim Software
среда 03 октября admin 88
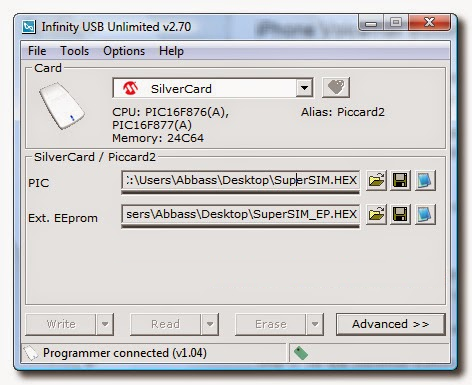
There are many reasons for which someone would like to clone his SIM Card. When I was living in Romania, I had always two – three phones in my pockets, each of them using different carriers in order to save money for my calls. Now, most of Romanian carriers gives thousands of free national minutes. After all, since October 2008 (portability launch date) is very difficult to understand which is the present carrier used by a phone number based on it`s prefix. My reason was financial one. Other people are using a 16 in 1 Super SIM (16 cloned SIM cards written on a single one), I don`t know for having the husband same number as his wife, for having on the same card the office number and the personal one, or just for illegal activities (Call Selling Operations: This type of fraud involves using stolen calling card numbers and /or cellular account numbers to sell less expensive cellular long distance (often international) service to others). Definition SIM cloning is the process in which a legitimate SIM card is duplicated.
1 SlMiFORQ is a forensic SlM card reader and cloning software. ASC is a mobile phone SIM card cloning suite for the purpose of examination,.
When the cloning is completed, the cloned SIM card’s identifying information is transferred onto a separate, secondary SIM card. The secondary card can then be used in a different phone while having all calls and associated charges attributed to the original SIM card.
The phrase SIM clone is often used to refer to the SIM card that has been successfully duplicated. A successful duplication hinges on the a user’s ability to extract the SIM card’s IMSI (International Mobile Subscriber Identifier) and Authentication key (Ki). While a IMSI is relatively easy to identify, finding the Ki can prove to be much more difficult for the novice user.
Separate devices and software programs may have to be used to decrypt the Ki. Engaging in activities that can result in a SIM clone is illegal. In the 1990s, companies that provided cellular services recognized the problems that SIM cloning presented and began to take measures to thwart the cloning business. New security measures such as embedding security operations make obtaining a SIM clone more difficult. Now, if a SIM card detects that cloning has been engaged, the SIM card can render itself inoperable. Whereas a few years ago cloning could be done by radio, people must now have physical access to the original SIM card. Though SIM cloning was easier with older models of cell phones and can still be technically done today, successfully completing a cloning is very difficult for some and virtually impossible for most.
Most of the technology currently available to facilitate cloning is meant to work only on older models of phones. Anti-tamper software on V2 of 3G SIM cards makes cloning new SIM cards and their corresponding devices a lost effort. As attractive as obtaining a SIM clone may seem to individuals who desire to use two phones with one phone number, legal and technical difficulties should discourage any efforts to clone SIM cards. It should also be noted that though using a clone can appear convenient in some respects, safety issues may also present themselves as a result of using the clone.
Law enforcement agencies may find it difficult to reach an injured or distressed party if an emergency call is made by a phone using a clone. This is because clones compromise the GSM location-based service that SIM cards rely on. What is Cell Phone Cloning Fraud? According to, in United States the Wireless Telephone Protection Act of 1998 expanded prior law to criminalize the use, possession, manufacture or sale of cloning hardware or software. Currently, the primary type of cell fraud is subscriber fraud. The cellular industry estimates that carriers lose more than $150 million per year due to subscriber fraud. Every cell phone is supposed to have a unique factory-set electronic serial number (ESN) and telephone number (MIN).
A cloned cell phone is one that has been reprogrammed to transmit the ESN and MIN belonging to another (legitimate) cell phone. Unscrupulous people can obtain valid ESN/MIN combinations by illegally monitoring the radio wave transmissions from the cell phones of legitimate subscribers.
Manual reparacion carburador bocar 2 gargantas vw parts. After cloning, both the legitimate and the fraudulent cell phones have the same ESN/MIN combination and cellular systems cannot distinguish the cloned cell phone from the legitimate one. The legitimate phone user then gets billed for the cloned phone’s calls. Call your carrier if you think you have been a victim of cloning fraud. A little history The early 1990s were boom times for eavesdroppers. Any curious teenager with a $100 Tandy Scanner could listen in to nearly any analogue mobile phone call. As a result, cabinet ministers, company chiefs and celebrities routinely found their most intimate conversations published in the next day’s tabloids. Mobile phone cloning started with Motorola bag phones and reached its peak in the mid 90’s with a commonly available modification for the Motorola brick phones, such as the Classic,the Ultra Classic, and the Model 8000.